Glove for Trezor Model T – Light Blue
12.00 $Light blue silicone glove for Trezor Model T, offering a snug fit and protective coverage.
Showing 49–64 of 144 results

Light blue silicone glove for Trezor Model T, offering a snug fit and protective coverage.

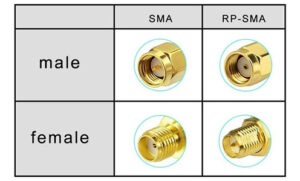
High-performance gold-plated SMA and RP-SMA RF connector adapters designed for low-loss, high-frequency signal transmission.
Engineered for secure, interference-resistant connections, these adapters ensure reliable mating between various RF interfaces.
Ideal for wireless communication systems, RF testing setups, and antenna integration projects. Gold plating provides superior conductivity
and corrosion resistance for long-term durability in demanding environments.


Industrial 4G LTE router with 150Mbps speed, supporting up to 16 users and external antennas for strong signal coverage.

Purchase the HackRF One, the ultimate Software-Defined Radio (SDR) for Lebanon’s tech enthusiasts and professionals.

The O.MG Cable is a hand made USB cable with an advanced implant hidden inside. It is designed to allow your Red Team to emulate attack scenarios of sophisticated adversaries. Until now, a cable like this would cost $20,000 (ex: COTTONMOUTH-I). These cables will allow you to test new detection opportunities for your defense teams. They are also extremely impactful tools for teaching and training.
The uncompromising attention to the physical size of the cable isn’t where we stopped. Thanks to continual firmware updates, the resulting power, flexibility, and ease of use have made the O.MG Cable a favorite for both new students and seasoned pros.

The Hak5 O.MG Plug is a discreet and powerful penetration testing tool for cybersecurity professionals in Lebanon. Launch payloads, log keystrokes, and secure networks with advanced functionality. Easy activation via the O.MG Programmer ensures the latest updates and seamless operation.


HAK5 Plunder Bug is a passive LAN tap for stealthy packet capture and network analysis—compact, USB-C powered, and available now in Lebanon.

The HAK5 Rubber Ducky Textbook – 2nd Edition is the definitive guide to mastering USB HID attacks and payload scripting using the iconic HAK5 Rubber Ducky. Updated with modern techniques, tools, and examples. Includes 40 exercises and 8 projects.

Hotplug attack, meet LAN. These pocket-sized pentest boxes perform network assessments in seconds!
As tiny Linux computers, they run DuckyScript™ payloads powered by Bash. Armed out-of-the-box with an ultra fast network scanner, you’ll get recon with the flick of a switch.
Or flip the switch to arming mode and sync up with the online library for a plethora of payloads — remote access, exfiltration & more.
With feedback by RGB LED, and now live in-shell with USB-C Serial on the NEW Cable edition.

The HAK5 Shark Jack Cable is a USB-C powered Ethernet attack tool for continuous payload deployment—compact, efficient, and now available in Lebanon.

Pull off the most creative and complex hotplug attacks.
The Hak5 USB Rubber Ducky, now in Lebanon, is a powerful keystroke injection tool disguised as a flash drive. Execute rapid payloads, bypass defenses, and customize attacks with DuckyScript™ 3.0 and Payload Studio. Perfect for cybersecurity professionals and red teams!


Protect your privacy with this compact hidden camera detector lens. Equipped with bright red LEDs, it helps you locate hidden cameras by revealing their lens reflections. Simply peer through the detector’s lens and scan your surroundings to spot concealed surveillance devices in seconds. Lightweight and portable, it’s perfect for travel, home, or office use. Stay secure and in control wherever you go!


HT627 multi-field EMF meter for detecting and measuring electric, magnetic, and RF radiation.


Handheld iCopy X100 RFID Programmer with color screen and all-frequency support—includes 5 x 125 kHz fobs , 5 x 13.56 MHz fobs, and ships quickly in Lebanon.


IPEX/U.FL to SMA or RPSMA Female RG178 cable, available in various lengths.

Connect internal RF modules to external antennas with this IPEX U.FL to SMA adapter cable. Available in 2 length options.